Information Technology
Good Links
Resources
- PSC – Help Desk Ticket
- Self-Service
- Canvas
- Webmail
- Starfish
- Dining Menu
- Webfiles
- Registrar
- Staff Council
- Sharing Portal
Calendars
College Catalogs
Working From Home
Get Help
If you have any questions, contact the PSC IT Services Help Desk at 518-327-6465 or Submit a ticket at https://paulsmithscollege.sysaidit.com/servicePortal/ using your PSC email and password . We will be available remotely to help you with your questions
Basics of Working Remotely
In case of an emergency, the ability to interact with employees and students in dispersed locations may become increasingly important. Paul Smith’s College Information Technology Services department provides tools to continue communications and maintain productivity.
Tech Tips: Backup, Backup, Backup!!!! 04/30/2018
As the end of the semester approaches, several students come into our office seeking help with fear in their eyes and a USB drive in hand. Normally, this means that a very important project, presentation, or Capstone can no longer be open on said USB drive. As much as we wish we could use our “IT magic” to bring the USB drive back to life, we often have to tell students the unfortunate news that their project is gone forever. What can you do to prevent this from happening to you? Just follow the three rules of keeping your important documents safe: BACKUP, BACKUP, & BACKUP. What are some ways to backup important data? Below are some solutions:
- Ask yourself, “Do I have this document in at least two locations?” An easy way of doing this is to save the file on both your local hard drive on your PC and on a USB drive.
- Email yourself your document as an attachment. Although you would have to do this every time you make a change, you at least have a restore point in the event you can’t access your up-to-date document.
- To the cloud! Today, cloud base storage is as easy as ever. Saving a document in the cloud allows you to keep your important documents off site where a 3rd party company will keep it safe. Here are some easy cloud-based solutions for you to use!
-
- OneDrive: This is accessible through your Paul Smith’s College account after logging into webmail.paulsmiths.edu.
- Storage/Cost: 1TB Free (with your Paul Smith’s College email account)
- Log into your account.
- Click the 3×3 grid in the top left corner.
- Click OneDrive.
- Storage/Cost: 1TB Free (with your Paul Smith’s College email account)
- Google Drive: If you have a Google account (or YouTube account), log into Google with either and you will already have a Google Drive for your account.
- Storage/Cost: 17GB Free (paid upgrades are available)
- DropBox: DropBox is another online solution that is strictly a cloud base storage system. In addition, it allows you to have a folder locally on your PC that automatically syncs with the cloud for a seamless backup solution.
- Storage/Cost: 2GB Free (paid upgrades are available)
- OneDrive: This is accessible through your Paul Smith’s College account after logging into webmail.paulsmiths.edu.
Happy saving and good luck on all your projects and presentations!
Tech Tips: Phishing – Direct Deposit 04/17/2018
Here at Paul Smith’s College, the IT Department is determined to keep our community well informed about current trends and best practices in technology. Besides usernames and passwords, phishing attackers may also try and trick you into filling out personal identifiable information in various ways. A way for this type of attack to look more legitimate is by disguising themselves as a person or group that may have influence over in some way. For example, an attacker may try to disguise their email account and message as someone from your organization’s Human Resource department. From here, the tactic of authority may come into play when they ask you to fill out information to adjust your direct deposit information. With this information, you may be providing the attacker all the personal identifiable information required to fill out a W-2 which can be used to compromise your finances.
Phishing Tips:
- Attackers will always try one of the following when it comes to creating a phishing email. If any of these apply to an email you receive asking for further action, you should immediately be skeptical:
- Authority – Sounding like you are an authority figure requesting legitimate information.
- Intimidation – Either subtle or more direct which could build an expectation of superiority.
- Consensus/Social Proof – Frequently gaining acceptance through group negotiation.
- Scarcity – Supply/demand
- Urgency – Buy it now before it’s too late! Do this thing now before there is serious disciplinary action.
- Familiarity/Liking – Creating trust through like minds and connection.
- No legitimate company, group, or person will request personal identifiable information from you unless you are the one who initiates the request.
- Example: Calling your bank to ask how much money you have in your account, and they verify your identify by asking for your last four digits of your Social Security Number.
- Feel free to forward any suspicious requests to IT or the department that is being impersonated by the attacker, rather than replying to the email.
If you have any questions pertaining to this tech tip, please do not hesitate to reply.
Cassidy Smith
Network Administrator
Contact Us »
Information Technology
Joan Weill Adirondack Library
Room 112
Hours: M-F, 8:00 am - 4:30 pm EST Monday-Friday
Closed holidays and weekends.
Department Phone: (518) 327-6465 (voicemail)
Tech Tips: Free Service – Virus Total 04/02/2018
Here at Paul Smith’s College, the IT Department is determined to keep our community well informed about current trends and best practices in technology. A free to use service called Virus Total allows you to scan any file, website, or other information to determine if it’s suspicious before interaction. This site works by running your entered content through over 70 antivirus scanners and URL/website blacklisting services. This service can be useful in the following ways:
- If you downloaded a file from a website that is new to you or suspicious in appearance.
- If you downloaded a file after realizing that you may have accidently downloaded something suspicious through an email or website.
- If you are about to go to a website that is suspicious or considered dangerous due to its offered content (i.e. free media).
Here is a link to the website: www.virustotal.com
Here is what the website looks like:
Feel free to check out other services offered through Virus Total to further increase your security online!
Tech Tips: Personal Devices and Interference 03/22/2018
Here at Paul Smith’s College, the IT Department is determined to keep our community well informed about current trends and best practices in technology. Wireless interference is when outside barriers and obstacles reduce the strength of wireless channels allowing connections to wireless devices. Because of interference, wireless connections may become slower and/or disconnect at random intervals.
Here are some devices that, when turned on, may cause interference:
- Microwaves (when turned on)
- BlueTooth devices (when BlueTooth is enable, active, and/or roaming)
- Wireless audio systems (most of these are BlueTooth)
- Refrigerators (when the motor kicks on)
Here are some common barriers and obstacles that will affect wireless signal strength:
- Refrigerators
- Wooden stand up closet
Here are some tips to reduce these obstacles:
- Each dorm room has one in-wall wireless access point with two wired ports with a light above the top port. If possible, attempt to rearrange your dorm room where a mini refrigerator and any big/bulky wooden furniture isn’t directly in front. The less physical objects in front of the in-wall access point, the better the signal strength will be.
- Disable wireless on your personal printer until you need to connect to it to print.
- Disable BlueTooth roaming on devices until you need to connect.
- Disable wireless on home wireless routers you may have in your dorm or office. Our network is designed so that these devices are no longer necessary. If you keep wireless enabled on your home router, you are causing interference to anyone nearby attempting to connect to PSC Wifi. If you feel that this device is necessary, please reach out to IT Helpdesk and we will be more than happy to assist!
If you have any additional questions pertaining to the information in this email, please don’t hesitate to ask 😊
Tech Tips: Phishing Attacks 11/27/2017
Defend Against Phishing Attacks
- Check for HTTPS – When submitting a username, password(s), and/or personal identifiable information (PII), always check the website domain name (URL). If it has https:// and “Secure” somewhere close by, then you are good to go! Here is an example for ps-portal.paulsmiths.edu:

If it doesn’t have https:// and “Secure” somewhere close by, then you are at risk for getting this information stolen. Here is an example of the fake site for ps-portal.paulsmiths.edu:
- Check a Link – If you see a link in an email asking you to click it, investigate where it will send you first. You can do this simply by hovering over it and seeing where the link will take you. Here is an example using the fake Help Desk email:
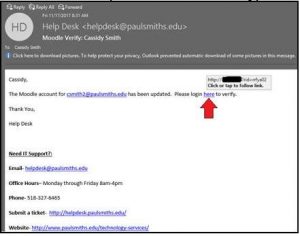
As you can see, the link appears to not be using https:// along with an obscure address. Although there is some grey area in what is a safe web link to click, at least be suspicious when seeing a site not using https://
- Analyze the Message – One of the easiest ways to trick users is exploiting the user directly. For example, some phishing attacks will send you a fake email notifying you of a problem with a recent “Amazon order”. Although you may not be expecting anything from Amazon, you may have a curious thought as to what the item may be. Some of us can quickly discredit that theory but others may not be able to. As a result, the user may fall victim to this attack.
Conclusion: Phishing attacks are not new, and will never go away. Although asking the IT Department about the legitimacy of an email may work, it is impossible for us to verify the legitimacy of every questionable email. It is up to you, the user, to know what to look for when you receive an email asking for you to perform certain actions. If you perform the steps to defend against phishing, you will have the tools you need to drastically reduce your odds on becoming a victim to a phishing attack.
Tech Tips: Identity Theft 09/21/2017
Here at Paul Smith’s College, the IT Department is determined to keep our community well informed about current trends and best practices in technology. This report is to highlight a recent identity theft attack involving Equifax, a global consumer credit reporting agency. About a week ago, the company release a statement stating that millions of users had their personal information stolen. If you think you have been affected by this incident, please click this link for more information.
NOTE: We advise you to not to do a free credit check through Equifax since they were responsible for the data breach in the first place.
Outside of this incident, please note that identity theft is a very common yet successful attack that compromises your personal information. Here are a few tips on how to detect and better prevent identity theft:
- Always be suspicious on anyone reaching out to you asking for personal information. Legitimate companies will not initiate a line of communication with you asking for personal information including the Paul Smith’s College IT Department.
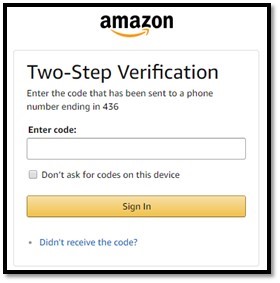
- If available, enable two-factor authentication on services you may use. For example, if two-factor authentication is enabled on your Amazon account, a PIN will be sent to a phone number you authorize (Figure 1). From here, you will need to enter your PIN into your Amazon login to continue. If an attacker had your e-mail and password, they would not be able to log in without the PIN. With this attempt, you would receive a PIN sent to your phone, but if you are not making a purchase, you will realize (hopefully) that someone is trying to log in Amazon with your e-mail and password.
- Use different and complex passwords for high-value services. For example, if you use the same password for your bank login and Facebook and your Facebook login information is stolen, then your bank account could also be compromised.
- Don’t use answers to security questions that can be discovered through social media. For example, if you have a security question of, “What high school did you go to?” and you share on Facebook that you’re about to go to your high school’s 10-year reunion, then an attacker can put two and two together, and answer your security question.
More information can be found here.
Figures
Figure 1: Two-Step Authorization page (Amazon
Tech Tips: Locking Your Computer Screen 08/07/2017
If you are ever signed into your Windows PC and you are stepping away from your PC, we strongly encourage you to press Windows Key (between your Ctrl and Alt key) + L.
If you are ever signed into your Mac device and you are stepping away from your device, we strongly encourage you to press Control+Shift+Eject (or Power if you do not have an Eject button).
What this does is prevents anyone from using your device without your permission. This also hides any personal or sensitive work you may be doing at the time. Here are some examples of what could happen if your device is left unattended and unlocked:
- A user posting something crazy on your Facebook timeline, and liking a “Nickleback Official Fanpage” (if you have Facebook open).
- A student changing his or her grades on Moodle.
- A user sending an email as you.
Tech Tips: Identifying Phishing Attacks 7/25/2017
To educate our users about information technology use, we want to share some information pertaining to a recent phishing attack. A phishing attack is when a malicious user emails/online messages you trying to disguise themselves as a legitimate source, or someone else you may trust. Here are some scenarios:
Scenario 1:
An email could be sent to you by what appears to be FedEx asking you to click a link for a status update. Although you are not expecting any packages, or if you’re not going through the already verified tracking number given to you for a legitimate package, you may be tempted to click the link.
Scenario 2:
An urgent email coming from what appears to be Helpdesk asking you to email back with your username and password stating that your account needs immediate attention.
Whenever you’re about to continue with an email, ALWAYS check where it is coming from not by the title name, but the full email address. Here is an example we were notified about this morning
NOTE: We are hiding the identity of the person who was being spoofed.
As you can see, the “From” field coming from someone from PSC doesn’t have the @paulsmiths.edu ending. Therefore, this message is almost certainly a phishing attempt.
If you have any further questions, please let us know. We are here to help the community be safer and more productive while using information technology.